STRATO Vault Key Storage
Overview
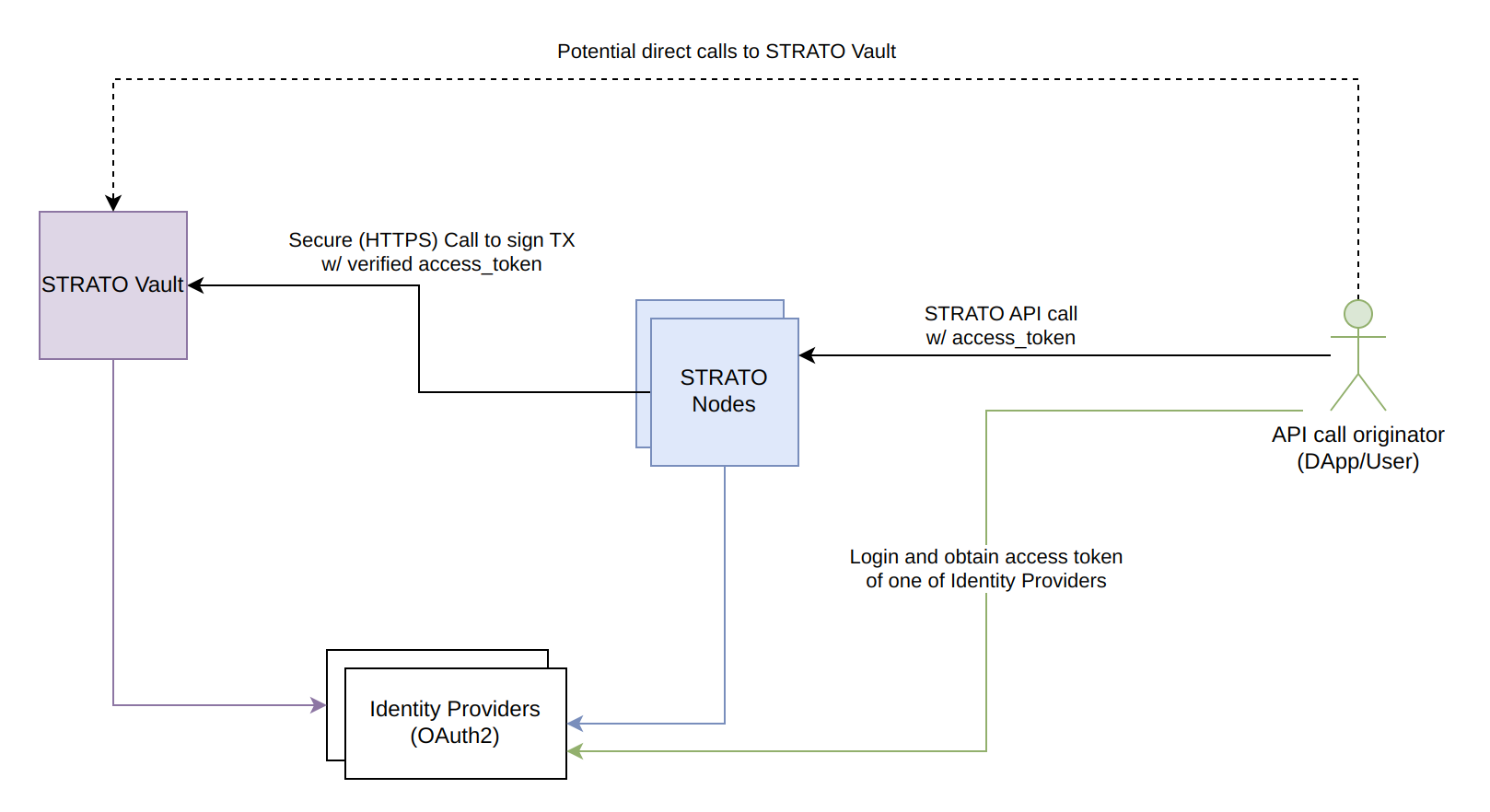
Vault is a secure encrypted database for user data. You can think of STRATO Vault's storage as a mapping from an OAuth2 user to a STRATO account. Vault is usually accessed by STRATO to gain information to sign transactions, but can also be called directly by the user via API. For each STRATO account created, STRATO Vault keeps the following user data in its database:
- Unique Identifier (matches the user unique identifier from the payload of JWT token)
- Encrypted private-key
- Encrypted blockchain address
- Automatically generated random salt string
- Identity Provider (OAuth2) provider associated with user
Encryption
All sensitive data stored in the STRATO Vault is encrypted using the hashing algorithm and the salt strings.
The STRATO implementation uses the unique random salt strings generated automatically for each of the users and stored along with their information in the database, and the STRATO Vault password, which is set by an administrator at the boot time of the STRATO network and where the password is only kept in memory.
Warning
STRATO Vault does not protect the users data from anyone who has the direct (SSH) access to the Vault machine. A person with this type of access can enter into the Vault's database and replace the users data stored there. Furthermore, they may extract the users keys from the Vault database if they know the Vault password.
Shared Vault
STRATO versions greater than or equal to v9.0 have different vault configurations. Prior to STRATO v9.0 there was a vault within each STRATO node. After 9.0, the vault component is a separate, external service, made accessible to multiple STRATO nodes. Thus now vault is a centralized key storage service, where nodes connect to and vault can be connected to an unlimited number of nodes.
The below is an in-depth diagram of the ineraction between Vault, a user and a single node.
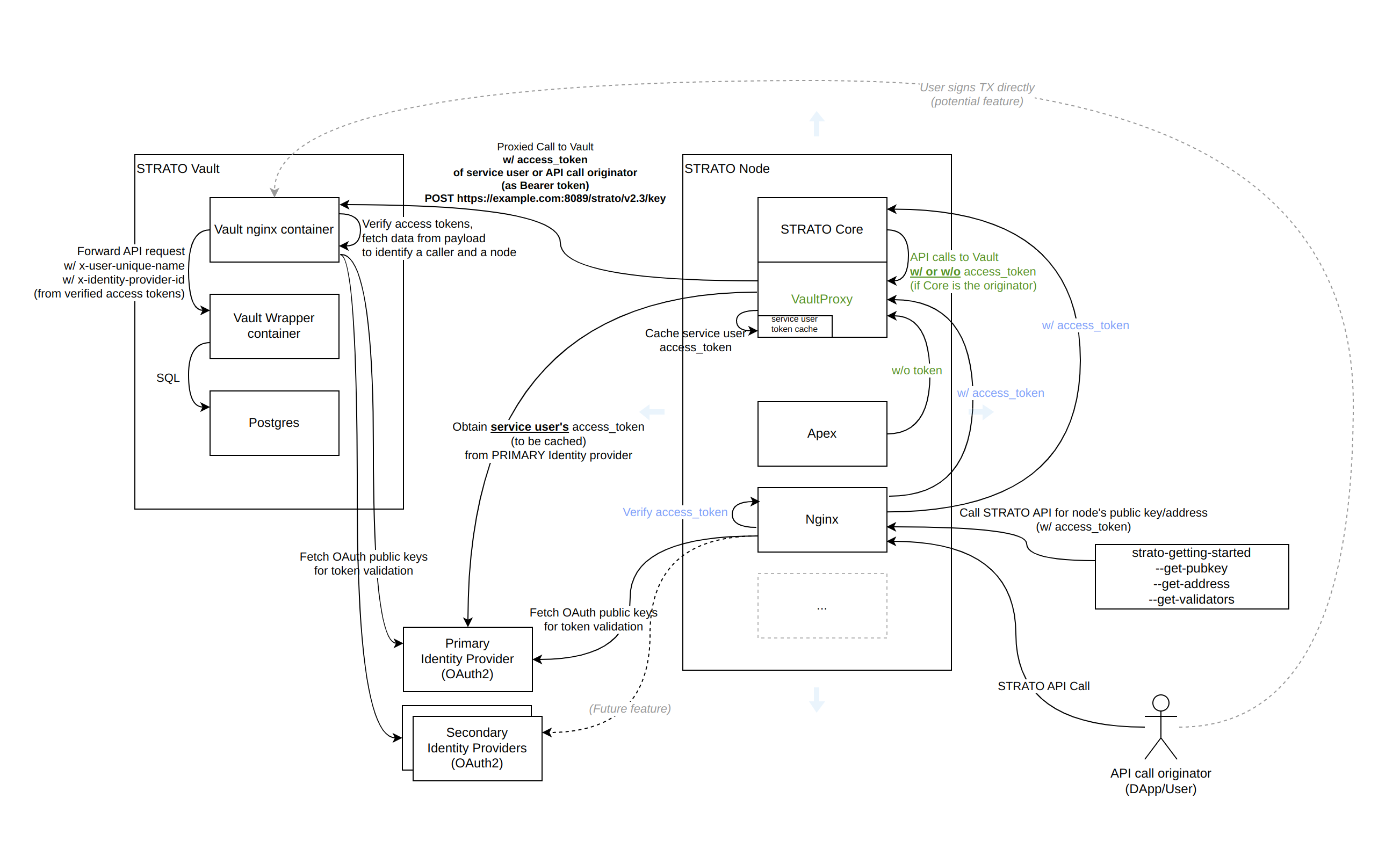
We can see in the bottom right corner a user making a transaction call to STRATO. Within STRATO, the call first interacts with a nginx service which acts as a reverse proxy and also verifies the access token. Nginx sense the request to the vault proxy, which is the intermediary service between the core of a STRATO node and an external vault. Vault Proxy calls Shared Vault which also confirms the access token is valid and attains the user data. The STRATO Vault in the diagram above is Blockapps Shared Vault service, but it is possible to have other 3-rd part Vault services. It is also important to note since STRATO v9.0 Vault supports multiple OAuth providers.
Tip
STRATO can be used without the vault to sign transactions. Instead STRATO allows users to manually prepare and sign their transactions with their own keys. See more in the Manual Identity Management Documentation.
Note
For more information about Vault deployment, see STRATO Vault Setup.